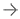According to the National Association of County and City Health Officials, only 33 percent of the organizations plan against cybersecurity threats and initiate patient identity protection protocols.
As the National Association of County and City Health Officials state, healthcare breaches remained to be costly and disastrous for the organizations in 2018. Each patient record exposure can cost up to $400, and hackers always try to access the medical information of hundreds of thousands of patients at once. Meanwhile, the National Association also notes that only 33 percent of the organizations plan against cybersecurity threats and initiate patient identity protection protocols.
Cybersecuity Threats Rolling Over Into 2019
Certainly, 2019 will only add fuel to the fire. Some of the most expected healthcare cybersecurity threats for this year are associated with increased personalization and selectivity, as well as social engineering. In particular, the trends lean toward malicious actors exploiting increasingly blurred boundaries between professional and personal activities. When people use their work accounts for accessing personal resources or follow the bring-your-own-device (BYOD) policy without precautions, it may lead to accidental data exposure or offer hackers a gateway into the individual’s workplace network.
Additionally, phishing is expected to become an even more advanced hacking approach, with scammers tuning up their emails and messages with the person’s information available from ad preferences and social media presence. We also should not forget about the ever-rising tide of identity thefts, when hackers access social security numbers and credit card data of their victims.
This increased focus on personalization in healthcare cybersecurity threats puts the majority of healthcare organizations in even higher danger. Apart from the direct and blunt software attacks, hackers will target the human factor as well, trying to violate data from the inside. If the providers are unable to defend themselves even at a basic level, they will not be able to allocate resources for further planning and mitigation of emerging threats.
So, the first step towards avoiding patient data breaches and cutting on settlement fines should be eliminating the known threats and system vulnerabilities regularly with the help of security testing automation. Testing automation brings in a major advantage for ensuring a provider’s infrastructure security. It tackles the basics, defining the most probable bottlenecks in different components of a single system as well as detecting integration loopholes between disparate applications and platforms.
Testing automation does not offer a silver bullet for the healthcare system security assurance and should go together with other testing techniques for more efficiency. However, it can cross out the known vulnerabilities to spare security testers’ time on exploratory testing and mitigating up-and-coming threats.
Below is an example of a roadmap for successful security testing automation. It shows possible applications, limitations, and processes beyond automated security tests.
Starting From a Thorough Health IT Asset Survey
Healthcare organizations’ internal IT infrastructures are systems with many elements, and each should be identified prior to testing automation. This inventory includes not only PCs, storage, servers, and installed software, but also corporate (or personal in case of BYOD) mobile devices, and medical devices too.
Mapping and understanding these physical assets, their location, purpose, and applications they run, security specialists can evaluate the risks and prioritize their testing activities.
Each asset’s risk can fall into one of the categories:
• Components (OS, firmware, patches, external applications)
• System-wide changes
• New software configuration errors
Risk categorization allows organizations both to find and focus on the most pressing vulnerabilities. It also helps to navigate across more common problems in healthcare software security, such as unpatched OS, poor authentication, inadequate security protocols, weak passwords and more.
Although quite trivial, these vulnerabilities might be the first target for hackers. Knowing that healthcare organizations can lack strong security policies in place, cybercriminals can resort to simpler attacks and still succeed in unauthorized data access. On the other hand, security testing specialists can automate continuous scanning and even eliminate such vulnerabilities.
Automating Cyber Security Tests
Based on the defined risks, security testing specialists can then segment the tasks for testing automation into functional, non-functional, application and infrastructure security scanning, as well as application logic testing groups. The testing teams can also define the success criteria to ensure that critical vulnerabilities are addressed in a way that benefits the organization in question.
One of the best practices implies that each application assigned for testing automation can be broken down into functions. This approach offers substantial application test coverage and helps to identify different vulnerabilities more effectively. Furthermore, security testing specialists can range the found vulnerabilities according to their severity and plan for fixes accordingly, either in a single upgrade or through multiple patches.
Launching Mock Cyber Attacks
While the series of automated tests helps to reveal vulnerabilities in certain system components, it still cannot ensure that the whole system will withstand a possible breach. To make sure that malignant activities do not lead to data exposure or theft, security testing specialists should initiate a mock-attack. It often focuses on such security basics as SQL injections, URL redirects, and open ports in the firewall.
Security testing teams should also identify sensitive systems, which can disrupt care delivery in case of an attack. Such systems can be devices related to acute patient care or surgery, for example, anesthesia monitors or dialysis machines. Depending on their sensitivity, such applications or physical assets should be accessed with limitations, or should not be targeted during the mock-attack at all to ensure patient safety.
Mock-attacks should be repeated from time to time to cover emerging vulnerabilities with system updates, new applications and devices. Certainly, they should be automated to save time and effort. This way, security testing specialists will be able to create a case scenario and then just tweak it to cover more variables instead of manually repeating the full processes.
Beyond Security Testing Automation
Once they are done with infrastructure security testing automation, security testers will get a whole knowledge base of the organization’s vulnerabilities, their range and severity. This information can be used as a foundation for further automation, such as for:
• Security workflows
• Continuous security monitoring tools
• Threat detection for preventing breaches
• Threat response
Best practices of care delivery keep changing, so health IT systems support flexible updates and upgrades by default. Yet, each new component in such a system creates both a promise and a potential vulnerability. Therefore, security testing should be considered an ongoing process to be enhanced, tweaked and repeated regularly.
Certainly, providers should consider using manual testing tools to explore upcoming threats and complement their automated testing results, occasionally shifting their focus between different activities. Only by staying flexible can healthcare organizations protect themselves both from basic and more advanced threats.
Editor’s note: The author, Maxim Chernyak, is a head of test automation and performance testing lab at A1QA, an expert in test automation methodologies and tools for functional and nonfunctional testing. Accountable for the education and adoption of state-of-the-art quality engineering practices by QA teams.


 January 28, 2026
January 28, 2026